RSA SecurID
the perfect combination of the advantages of RSA SecurID authentication and the convenience and sensitivity of risk-based authentication.
Overview
provides flexibility and convenience through risk-based authentication technology
• Deploy risk-based authentication technologies in addition to software and hardware tokens
Reduce your company's authentication costs and expand its use
Reduce Total Cost of Ownership
• Use a set of built-in features to complete the most time-consuming and expensive tasks related to managing enterprise authentication suites
• Allow your IT staff to complete more tasks in less time
Give Full Play to the Potential of Virtual Environment
Make the most of your company's virtualized environment to simplify deployment, management, and ongoing system management
Leverage your existing infrastructure and virtualization technology
Security is an increasingly serious challenge for some companies to manage shrinking IT budgets and provide security measures for more users. This problem is exacerbated by users who use unmanaged mobile devices to access sensitive data through uncontrolled access points such as portals. Companies must deploy strong authentication measures to meet more and more challenges.
RSA®Authentication Manager 8.0 delivers world-leading RSA SecurID®Authentication technology now provides a risk engine designed to meet the goals and needs of today's companies. RSA Authentication Manager is designed to verify authentication requests and centrally manage user authentication policies for accessing enterprise networks.
compared with any other system on sale today, RSA Authentication Manager can use various RSA SecurID tokens to provide two-factor user authentication to more virtual private networks (VPN), wireless networks, web applications, business applications and operating environments. RSA Authentication Manager virtual devices are flexible enough to support various authentication methods, advanced risk engines, easy to manage, and can interoperate with industry-leading products and suppliers.
the power of risk-based analysis
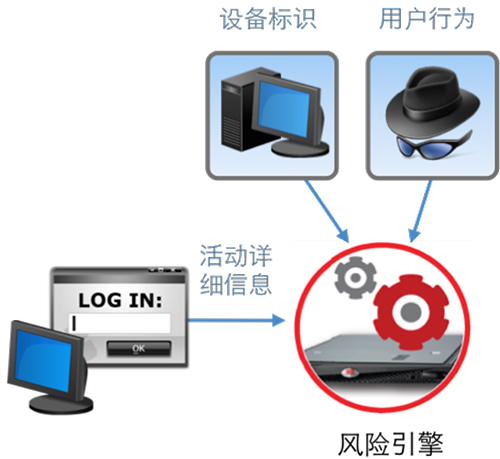
RSA Authentication Manager8.0 provides risk-based authentication (RBA) technology that can be optionally licensed and designed to significantly improve security. RBA retains a similar username/password login experience, bringing convenience to end users. Users need to provide additional identification only if the login attempt is considered a high-risk behavior. During the period when "progressive" authentication is required, users can provide additional identification by answering life-related questions or completing on-demand (SMS) authentication.
Risk-based authentication
RBA is designed to protect access to the most commonly used web applications such as SSL VPN, portals, Outlook Web Access (OWA) and Microsoft SharePoint environments. With RBA joining RSA Authentication Manager product line, companies are now able to ensure secure access to more applications in a more cost-effective way than ever before.
RSA Risk Engine is a mature technology that can support the most convenient strong authentication methods. The risk engine is not a static, rule-based system. It combines real-time equipment and behavior analysis, and can dynamically adjust its risk model when collecting new information. It can perform transparent authentication for low-risk users, while high-risk users will be prompted to provide additional identification. RBA can provide strong authentication, which is low cost and convenient for end users and IT administrators.
manageability
RSA Authentication Manager includes some built-in features that can solve the most time-consuming and expensive tasks related to managing enterprise authentication suites. The user dashboard is a convenient single-pane view designed to allow service desk administrators to quickly resolve the most common user query requests without running multiple reports or multiple searches. The customizable self-service console allows users to manage their own authentication methods and is another feature that can save IT staff time. The self-service portal is deployed in the DMZ area of the network, allowing users to change their PIN, apply for token replacement, apply for emergency access, and use other troubleshooting services.
User dashboard
Resolve the most common user query requests in a single-pane view
Real-time monitoring of recent authentication activities
• Manage tokens
o Enable/Disable
o Assign more tokens
o Unlock/Lock
o Clear PIN
View user group membership and accessible agents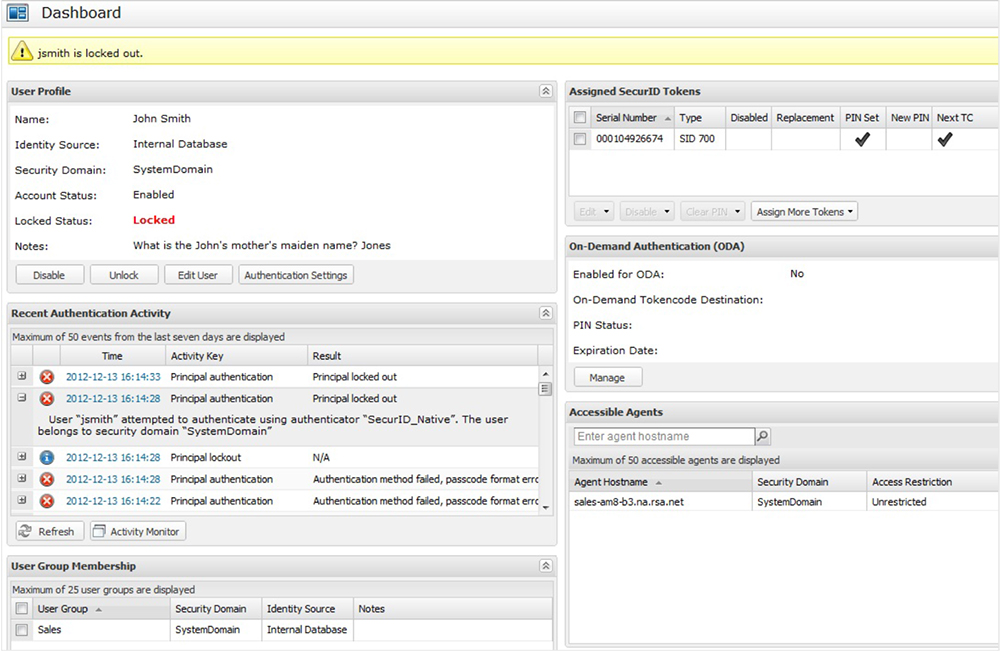
Give Full Play to the Potential of Virtual Environment
RSA Authentication Manager enables companies to fully utilize VMware ESX or ESXi virtualization, greatly simplifying deployment. Virtualization can also improve manageability. Simplified patch installation allows companies to quickly update their systems. The updates of the virtual device, the underlying operating system and RSA Authentication Manager software are all in one service pack, so there is no need to worry about managing different layers of the system separately.
interoperability
RSA Authentication Manager can interoperate with many major network infrastructure and operating system products on the market. The Secured by RSA program is one of the largest alliance programs of its kind, bringing together hundreds of complementary solutions. Secured by RSA includes more than 400 products from more than 200 suppliers, ensuring the company achieves maximum flexibility and investment protection. Leading remote access products, VPN, firewall, wireless network equipment, web server and commercial application vendors all integrate support for RSA Authentication Manager in their products.
EMC2, EMC, EMC logo and RSA] are registered trademarks or trademarks of EMC Corporation in the United States and other countries. VMware is a registered trademark of VMware, Inc in the United States and other jurisdictions.©2013 EMC Corporation Copyright. All rights reserved. S. printing. 0113
Table H11403
EMC believes that the information in this document is accurate as of the date of release. Information is subject to change without notice.