Homepage>product center>security analysis> Paloalto
Paloalto
Please enter the text......
-
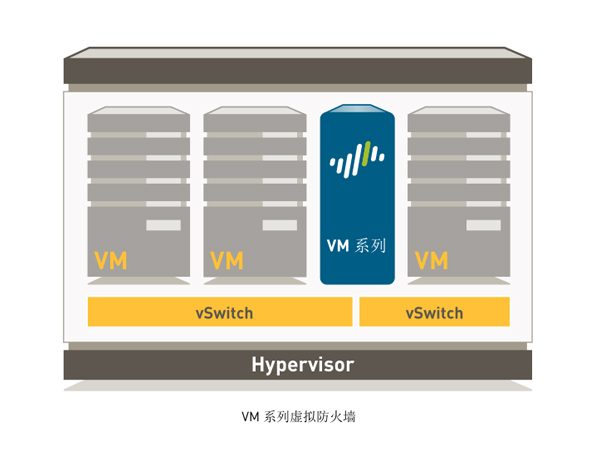
specsheet-VM series
through App-ID™All applications are classified at each port at all times.
• Identify applications regardless of ports, encryption (SSL or SSH) or circumvention techniques.
uses applications (not ports) as the basis for all security enable policy decisions: allow, reject, schedule tasks, check, and apply traffic shaping.
to conduct in-depth analysis of unrecognized policy control applications, threat forensics, creation of custom App-ID, or packet grabbing.넶287 ¥ 0.00 -
specsheet-pa-5000
through APP-ID™Classify all applications on each port at all times.
• Identify applications regardless of ports, encryption (SSL or SSH) or circumvention techniques.
uses applications (not ports) as the basis for all security enable policy decisions: allow, reject, schedule tasks, check, and apply traffic shaping.
to conduct in-depth analysis of unrecognized policy control applications, threat forensics, creation of custom App-ID, or packet grabbing.넶12 ¥ 0.00 -
specsheet-pa-3000
through APP-ID™All applications are classified at each port at all times.
• Identify applications regardless of ports, encryption (SSL or SSH) or circumvention techniques.
uses applications (not ports) as the basis for all security enable policy decisions: allow, reject, schedule tasks, check, and apply traffic shaping.
to conduct in-depth analysis of unrecognized policy control applications, threat forensics, creation of custom App-ID, or packet grabbing.넶7 ¥ 0.00 -
specsheet-pa-500
through APP-ID™All applications are classified at each port at all times.
• Identify applications regardless of ports, encryption (SSL or SSH) or circumvention techniques.
uses applications (not ports) as the basis for all security enable policy decisions: allow, reject, schedule tasks, check, and apply traffic shaping.
to conduct in-depth analysis of unrecognized policy control applications, threat forensics, creation of custom App-ID, or packet grabbing.넶8 ¥ 0.00